Creating a keytab for application serversThis guide will show you how to create and use a keytab file for your app server. Summary Keytab files are not required. There are alternatives to using keytab files. One alternative is to simply provide a username and password instead of the path to a keytab file. Keytab files can be used by clients to authenticate to an app server or they can be used by app servers to pre-authenticate to the KDC. An app server must first authenticate to the KDC before it can authenticate client requests. The SPNEGO Http Servlet Filter gives you the option of either specifying a username/password in the web.xml file or specifying the location of the keytab file in the login.conf file. Before Getting Started Be sure that you have read and successfully performed ALL of the steps in the pre-flight documentation before proceeding any further. It is imperative that you perform all steps in the pre-flight since we will be using files that we created from that guide. If you don't already have a working app server that authenticates requests via Kerberos/SPNEGO, take a look at the installing Tomcat or installing JBoss example. It is necessary that you read through and perform the steps in the Tomcat or JBoss install guide. The rest of this guide will use information provided during the install and configuration of your Tomcat or JBoss server. Once your app server is running and your able to get SPNEGO authentication working properly using Internet Explorer (by default FireFox will prompt), the final step in the pre-requisite for this guide is for you to read through and perform the steps in the Creating a Keytab for Java Clients guide. Creating the keytab file If you have read and performed the steps as described in the Creating a Keytab for Java Clients guide, then you already know how to create a keytab for app servers. With respect to the keytab file structure itself, there is no difference between a keytab for client apps, and one for app servers; you create either one exactly the same way. We will use the same process we used in the Creating a Keytab for Java Clients guide to create a keytab file for our app server. But first we must recall the username and password our app server uses by looking at the web.xml file. 
To generate a keytab for the server, open a command prompt and 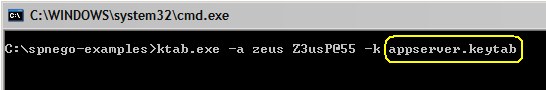
Notice that our keytab file is named Testing the keytab file Before we can test the keytab using HelloKeytab.java, we must modify the login.conf file we created during the Creating a Keytab for Java Clients guide. Also, we must change the path to point to the newly named/created keytab file as well as change the principal name. 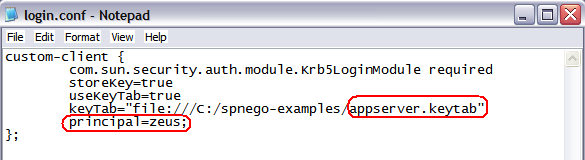
We can now test our keytab file by running the HelloKeytab.java
program we modified earlier by typing the command 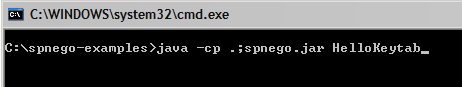
If all is well, you should get an output similar to the following: 
Configuring the app server to use keytab file Note: some app servers will automatically restart if it detects any changes to any conf files or web.xml files. Stop the app server before making any changes. 1) Move the appserver.keytab to the same directory as the login.conf file. 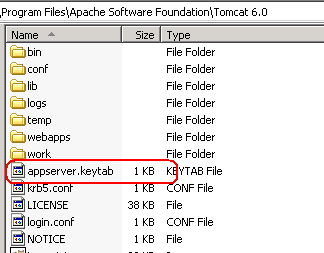
2) Modify the app server's login.conf file to reflect usage of a keytab file. 
Notice that the path to the 3) Remove the username and password from the web.xml file 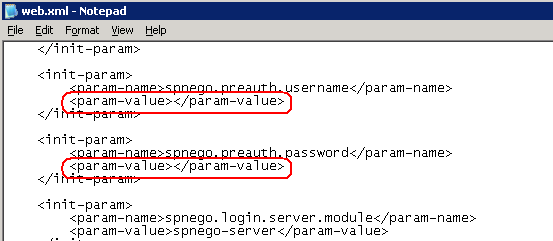
Configuration is now complete. Restart your app server. Testing the new configuration Open IE and go to 
Changing app server's pre-auth username Extra care must be used if sometime later you decide to change the username that your app server uses for pre-authentication. For example, in the Tomcat install guide, we specified
that our app server will use the Windows NT (Domain) account named Before we can use a new username, we must first un-map/de-register/delete the SPN(s) that
are registered/tied-to the 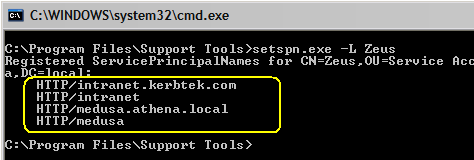
We then use the setspn.exe tool to first delete each registered SPN and then to create/register each deleted SPN to the new username. NOTE: an SPN must only be registered to one and only one username (many-to-one). However, the converse is not true; a username may have more than one SPN registered (one-to-many).
Links:
Troubleshooting:
Examples:
Licensing:
© 2009 Darwin V. Felix. All rights reserved.
|